How to outbound external connection of GN3 devices over remote server?
I use GNS3 simulator to study network feature sometimes. There is many instruction over internet. In this post, I will introduce how to use NAT fuction to connect to interet for outbound traffic.
1. Pre-requisite.
I have local GNS3 client and remote server over Packet.net and AWS Baremetal cloud. In my case, my remote server is the Linux (Ubuntu 16.04) host. After then, I uploaded CiscoNX v9000 in my remote server.

This is the my environment to re-produce in this post.
2. About NAT appliance (DHCP feature).
In GNS3, there is NAT appliance. It has the role to connect the physical interface on remote server virtually. This NAT appliance offers DHCP feature to assign IP address. This IP address determined the next hop against the Cisco switch/router. Thus, the Cisco switch/router should have DHCP feature.
|
feature dhcp ip route 0.0.0.0/0 192.168.122.1
no ip dhcp relay no ipv6 dhcp relay
interface Ethernet1/1 no switchport ip address dhcp no shutdown |
After this configuration, I can verify the interface status with "show ip int br" command
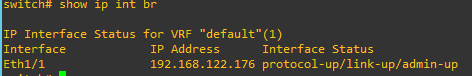
And "ip route 0.0.0.0/0 192.168.122.1" is written. In the Linux host (remote server), I can see the interfaces like below.

With this interfaces, the packet will transfer to external side. I can see the masqurade rule in "iptables table" like below.

Now, I can send traffic to outside on switch 1. Please noteh that it is not possible on switch 2.
|
switch 1(config)# ip domain-lookup
|
3. Configuration NAT Inside and Outside
Switch 1 can send the packet to outside, however switch 2 can not. Because "192.168.122.0/24" network can only be masquraded in the remote server. This is the reason why the switch 1 has NAT feature. In this instruction, there is the explation for Cisco NAT concept.


Inside source translation is for inside --> outside traffic. Outside source translation is for outside --> inside traffic. At first, I will make the direction on Cisco switch 1.
|
feature nat interface Ethernet1/1 no switchport ip address dhcp ip nat outside no shutdown interface Ethernet1/2 no switchport ip address 172.12.1.12/16 ip nat inside no shutdown |
4. Create Rule (NAT Policy) for outbound traffic.
In this post, I handle only outbound traffic. The main factor is that IP address for all traffic to outside should be changed with Switch 1 interface ethernet 1/1 IP address. In this post, It will be useful. I want all traffic to be sent.
|
ip access-list 1
|
5. Configure inside network (Switch 2).
So far, I made NAT firewall. From this part, it can assume internet network. However, I only use single switch/router simply.
|
ip route 0.0.0.0/0 172.12.1.12 interface Ethernet1/2 no switchport ip address 172.12.2.12/16 no shutdown |
This is normal configuration. There is nothing special. After default configuration. I can verify the outbound connection like below over switch 2.

It works now.
Reference
[ 1 ] https://docs.gns3.com/1c2Iyiczy6efnv-TS_4Hc7p11gn03-ytz9ukgwFfckDk/index.html
[ 2 ] https://docs.gns3.com/appliances/cisco-nxosv9k.html
[ 3 ] https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/7-x/interfaces/configuration/guide/b_Cisco_Nexus_9000_Series_NX-OS_Interfaces_Configuration_Guide_7x/b_Cisco_Nexus_9000_Series_NX-OS_Interfaces_Configuration_Guide_7x_chapter_01100.html#concept_F5BFDE98ABA749859F5AD710AC61EFCD
[ 4 ] https://onlyit.tistory.com/entry/How-to-use-a-nat-node-in-gns3
'Network Engineering > OpenSource' 카테고리의 다른 글
| How to configure Simple Internal BGP with Route Reflector over FRRouting (include Installation)? (0) | 2020.06.03 |
|---|---|
| How to configure Internal BGP and Router Reflector with Bird? (0) | 2020.05.11 |
| How to configure External BGP with Bird? (0) | 2020.05.10 |
| How to Configuration VXLAN in Ubuntu 16.04 (0) | 2018.08.16 |
| How to Configure “ipvsadm” in Ubuntu (0) | 2018.08.10 |